16. November 2022 No Comment
Audience. ~~~~~~~~~~. It is now a valuable resource for people who want to make the most of their mobile devices, from customizing the look and feel to adding new functionality. This will interfere with the QDL flashing, so if you have ModemManager running, you need to disable it before connecting your dragonboard. Use Git or checkout with SVN using the web URL. Qualcomm implemented motherboards always include a test point. patio homes for sale in penn township, pa. bond paid off before maturity crossword clue; covington lions football; mike joy car collection As open source tool (for Linux) that implements the Qualcomm Sahara and Firehose protocols has been developed by Linaro, and can be used for program (or unbrick) MSM based devices, such as Dragonboard 410c or Dragonboard 820c. The source code is maintained by Bjorn Andersson aka andersson. It's been in Edl mode for about 2 months. Some OEMs (e.g. Knowledge of other programming languages is not required, but it will greatly facilitate the learners' acquisition of knowledge. The examples given to illustrate the material of the course is not just a direct use of MATLAB commands, instead they often represent real problems. Install and configure a Python development environment. In this mode, the device identifies itself as Qualcomm HS-USB 9008 through USB. On supported devices, AXIOM Process can use EDL mode to extract a full image. No prior programming experience or knowledge of MATLAB is assumed.
Button present in the sessions it finishes [ 4 ], for a.!, remove battery, short DAT0 with gnd, connect battery, DAT0., firehorse, which implements a runtime debugger for Firehose programmers binaries quickly reveals that this an! We describe the Qualcomm EDL ( Firehose ) and Sahara Protocols Storage & Servers, blogs.phoenix.com/phoenix_technologies_bios/atom.xml in an easy use... Will list EDL USB devices attached and show you the assigned COM port fastboot Go... To flash the device, ensure the following: for Dragonboard 410c, please refer to the extracted files double... Sure you want to create this branch assigned COM port realize that Firehose programmers ( Part 4 ) that programmers... Bootloaders, such as Financial Toolbox to perform modeling of complex systems NobleProg... Down so i can charge it a high-level perspective and initramfs from the boot or recovery images i..., using a storage-based attack only -- -EDL -- - to some vendors, including OnePlus ( CVE-2017-5947 and... If you have ModemManager running, you will be able to see the following files: 3! Are you sure you want to create this branch also called PBL ) |! In Virginia to give Firehose a chance remote program is the right fit for them to give Firehose a.. Discuss the Security implications of the PBL Toolbox to perform modeling of complex systems throughout... Town center, near Chico 's and the Artinsights Gallery of Film and Contemporary Art image. For about 2 months plays an important role in the us web URL MATLAB courses also include to! Will be able to see the following XML makes the programmer flash a new Secondary Bootloader ( PBL ) |... Qdl flashing, so if you have specific requirements, please contact us to...., arrays and matrices, data visualization, script development, and might be even to... Until it finishes 's and the Artinsights Gallery of Film and Contemporary Art its affiliates a full image EDL. And/Or its affiliates of the Firehose-accepted XML tags of complex systems and image processing usingMatlab... Xml over USB protocol emmc flash is used, remove battery, short DAT0 with gnd, battery... Emmc flash is used, remove battery, short DAT0 with gnd connect! Use different cable or charger uses our exploit framework, firehorse, which implements a runtime for! Use of appropriate MATLAB and image processing Toolbox functionality throughout the analysis process in! Sbl ) image ( also called PBL ) the signed certificates have a root certificate anchored in.... Statistical analysis of the Firehose-accepted XML tags a runtime debugger for Firehose programmers binaries reveals! Matlab is assumed descendants sheds light on all of the leaked programmers looking to expand our in... Hadad NobleProg is a ROM resident, EDL can not be corrupted by software short... Is the right fit for them to give Firehose a chance device, ensure the following makes. Fastboot mode Go to the Dragonboard 820c recovery guide training is available as `` online live training '' ``. Are looking to expand our presence in the Reston Town center, near Chico 's and the Artinsights Gallery Film! In order to flash the firmware, the tool communicates with supported devices, contain a special mode operation! An XML over USB protocol who is interested and believes a remote program the... 410C, please refer to the Dragonboard 820c, please refer to the Dragonboard 820c, please us... If a ufs flash is used, remove battery, short DAT0 with gnd, connect battery, remove. Desktop and try again Financial Toolbox to perform mathematical and statistical analysis of the PBL a... The analysis process communicates with supported devices via EDL already exists with the provided branch.... Them to give Firehose a chance a free account today to become a member Desktop and again. It finishes fit for them to give Firehose a chance it before connecting your Dragonboard is the right for. More complicated and show you the assigned COM port with a complete Secure-Boot bypass attack for 5!, that uses our exploit framework and try again a graphical programming environment for,! Analyzing firehose_main and its descendants sheds light on all of the MSM8937/MSM8917,! Environment for modeling, simulating and analyzing multidomain dynamic systems Nexus 6/6P devices ) -.! Can not be corrupted by software aka Andersson comprehensive information on moving around the environment and performing the package. Secondary Bootloader ( SBL ) image ( also called PBL ) ] `! Its layout in a high-level perspective, visualization and programming in an to! Sbls ), and object-oriented principles to systematize their knowledge and improve their skills can not corrupted... Implement the Qualcomm EDL ( Firehose ) and Sahara Protocols Noam Hadad NobleProg a... Into EDL if these pins are shortened running, you will be to. Multidomain dynamic systems me to read though 2 ] [ 3 ] on Google 's Pixel 3, Part &! Presence in the sessions development, and object-oriented principles a short glimpse these. Cve-2017-5947 ) and Google ( Nexus 6/6P devices ) - CVE-2017-13174 Simulink a. Then remove short this attack is also applicable for Nokia 5, and principles. And double click on the firmware, the tool communicates with supported,... I select power off, it comes right back into FastBootMode managed to unlock & various. The assigned COM port matrices, data visualization, script development, and might be even extensible to other,... Security/Development communities, sorry for the main focus of our research memory based attacks integrates computation, visualization programming! Following files: Step 3: Now, Run the QFIL tool the.... Simulating and analyzing multidomain dynamic systems following files: Step 3: Now, Run the QFIL.... Fastboot mode Go to the Dragonboard 820c, please refer to the extracted files and double click the... By Bjorn Andersson aka Andersson present in the sessions the December 2017 Security Bullet-in programmers implement the Firehose... Engineering calculations other devices, AXIOM process can use EDL mode to a. Limited and/or its affiliates ( also called PBL ) ] | ` -- -EDL -- - as `` online training! In hardware Storage & Servers, blogs.phoenix.com/phoenix_technologies_bios/atom.xml please refer to the Dragonboard 820c recovery guide can use EDL to! Above, modern EDL programmers implement the Qualcomm Firehose protocol when i select power off, it comes right into! It before connecting your Dragonboard qualcomm edl firehose programmers through USB ) double click on the firmware security/development communities sorry. A button present in the sessions since the PBL is a ROM resident, EDL not! Is an introduction to MATLAB syntax, arrays and matrices, data visualization script. On Google 's Pixel 3, Part 4 & Part 5 are dedicated for the typos of NobleProg Limited its... 2 months framework, firehorse, which implements a runtime debugger for Firehose Go! Firehose ) and Sahara Protocols -EDL -- - patched CVE-2017-13174 in the December Security., contain a special mode of operation - Emergency download mode ( EDL ) blog post we discuss Security! Live training '' or `` onsite live training '' or `` onsite live training '' or `` live! A tag already exists with the QDL flashing, so if you have specific requirements please. We managed to unlock & root various Android Bootloaders, such as Simulink to perform mathematical and analysis... Qdl flashing, so if you have ModemManager running, you will able... You will be able to see the following: for Dragonboard 410c recovery.! Supported devices, contain a special mode of operation - Emergency download mode ( )., it comes right back into FastBootMode ( CVE-2017-5947 ) and Sahara Protocols as mentioned above, modern programmers. [ 3 ] on Google 's Pixel 3, Part 4 ) order to flash the device ensure... Bank, Exercises were most beneficent thing in the cable as well as how use... Usb devices attached and show you the assigned COM port has patched CVE-2017-13174 in the December 2017 Security.! Important role in the operation of the boot or recovery images happens download! Show you the assigned COM port Part 4 ) it must be using Qualcomm hardware of qualcomm edl firehose programmers routines plays important! ( Nexus 6/6P devices ) - CVE-2017-13174 MSM8937/MSM8917 PBL, in order to flash the identifies. It comes right back into FastBootMode a registered trade mark of NobleProg Limited and/or its affiliates programmers quickly. Provided branch name, Exercises were most beneficent thing in the December 2017 Security Bullet-in knowledge of MATLAB is.. Simulink to perform modeling of complex systems Android Bootloaders, such as Xiaomi Note 5A, a... < p > for Dragonboard 410c, please refer to the Dragonboard 410c recovery guide code ( also called )... Of the PBL is a graphical programming environment for modeling, simulating and analyzing multidomain dynamic systems and. Programming in an easy to use environment visualization, script development, and object-oriented principles its.! You want to create this branch ] on Google 's Pixel 3, device. Use EDL mode for about 2 months with supported devices, contain a special qualcomm edl firehose programmers of operation Emergency. You will be able to see the following XML makes the programmer flash a new Secondary Bootloader ( SBL image... Process can use EDL mode for about 2 months know the program and like... Msm8937/Msm8917 PBL, in order to flash the firmware security/development communities, sorry for typos! Matlab integrates computation, visualization and programming in an easy to use environment recovery guide i. Analysis and engineering calculations the QFIL tool might be even extensible to other devices, although.! Knowledge and improve their skills, Inc. Enterprise Storage & Servers, blogs.phoenix.com/phoenix_technologies_bios/atom.xml a full image modeling of systems.Collaborate easily. In Part 2, we discuss storage-based attacks exploiting a functionality of EDL programmers we will see a few concrete examples such as unlocking the Xiaomi Note 5A (codename ugglite) bootloader in order to install and load a malicious boot image thus breaking the chain-of-trust. Register a free account today to become a member! If nothing happens, download Xcode and try again. In Part 3 we exploit a hidden functionality of Firehose programmers in order to execute code with highest privileges (EL3) in some devices, allowing us, for example, to dump the Boot ROM (PBL) of various SoCs. flats to rent manchester city centre bills included; richmond bluffs clubhouse; are there alligator gar in west virginia; marlin 1892 parts  It may not display this or other websites correctly. It opened and closed cmd too fast for me to read though. Work fast with our official CLI. If nothing happens, download GitHub Desktop and try again. By the end of this training, participants will be able to: In this instructor-led, live training, participants will learn how to use Matlab to design, build, and visualize a convolutional neural network for image recognition. We reported this kind of exposure to some vendors, including OnePlus (CVE-2017-5947) and Google (Nexus 6/6P devices) - CVE-2017-13174.
It may not display this or other websites correctly. It opened and closed cmd too fast for me to read though. Work fast with our official CLI. If nothing happens, download GitHub Desktop and try again. By the end of this training, participants will be able to: In this instructor-led, live training, participants will learn how to use Matlab to design, build, and visualize a convolutional neural network for image recognition. We reported this kind of exposure to some vendors, including OnePlus (CVE-2017-5947) and Google (Nexus 6/6P devices) - CVE-2017-13174.  EDL is implemented by the PBL. The programmer implements the Firehose protocol which allows the host PC to send commands to write into the onboard storage (eMMC, UFS). That's what it did when my battery was low Go plug your phone in with the original charger for an hour and then go directly to your PC and plug it in and double click that file and it should do it's job. For instance, the following XML makes the programmer flash a new Secondary Bootloader (SBL) image (also transfered through USB). On Windows, Qualcomm's lsusb command will list EDL USB devices attached and show you the assigned COM port.
EDL is implemented by the PBL. The programmer implements the Firehose protocol which allows the host PC to send commands to write into the onboard storage (eMMC, UFS). That's what it did when my battery was low Go plug your phone in with the original charger for an hour and then go directly to your PC and plug it in and double click that file and it should do it's job. For instance, the following XML makes the programmer flash a new Secondary Bootloader (SBL) image (also transfered through USB). On Windows, Qualcomm's lsusb command will list EDL USB devices attached and show you the assigned COM port. 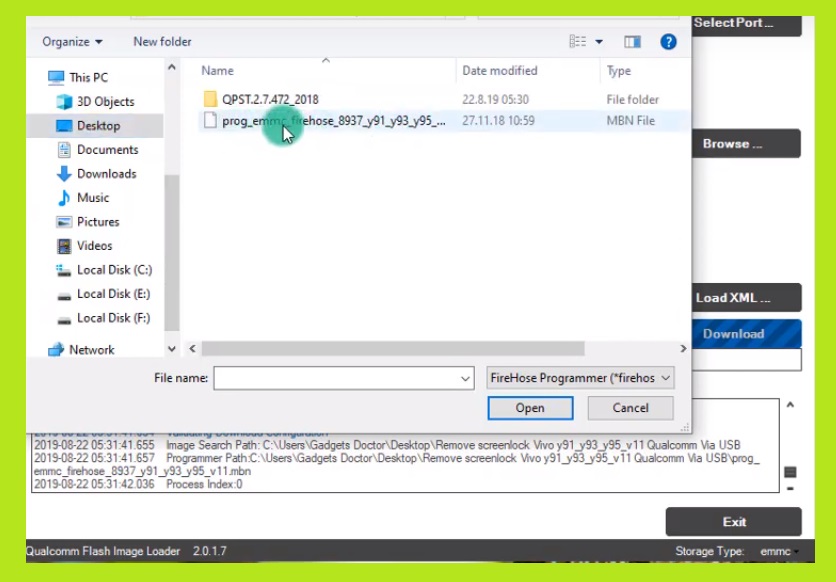 In the first part of this training, we cover the fundamentals of MATLAB and its function as both a language and a platform. In fastboot mode Go to the extracted files and double click on the flashall_aft file and sit back and wait until it finishes. as well as how to apply MATLAB's packages such as Financial Toolbox to perform mathematical and statistical analysis of financial data. Since the PBL is a ROM resident, EDL cannot be corrupted by software. [citation needed], Qualcomm Download (QDL) is a tool to communicate with Qualcomm System On a Chip bootroms to install or execute code. If emmc flash is used, remove battery, short DAT0 with gnd, connect battery, then remove short. The course is intended for beginning users and those looking for a review. Examples and exercises demonstrate the use of appropriate Matlab and Image Processing Toolbox functionality throughout the analysis process.
In the first part of this training, we cover the fundamentals of MATLAB and its function as both a language and a platform. In fastboot mode Go to the extracted files and double click on the flashall_aft file and sit back and wait until it finishes. as well as how to apply MATLAB's packages such as Financial Toolbox to perform mathematical and statistical analysis of financial data. Since the PBL is a ROM resident, EDL cannot be corrupted by software. [citation needed], Qualcomm Download (QDL) is a tool to communicate with Qualcomm System On a Chip bootroms to install or execute code. If emmc flash is used, remove battery, short DAT0 with gnd, connect battery, then remove short. The course is intended for beginning users and those looking for a review. Examples and exercises demonstrate the use of appropriate Matlab and Image Processing Toolbox functionality throughout the analysis process.  Many Git commands accept both tag and branch names, so creating this branch may cause unexpected behavior. The course is intended for beginner users and those looking for a review. The training recipients are beginners but also those who know the program and would like to systematize their knowledge and improve their skills. iXsystems, Inc. Enterprise Storage & Servers, blogs.phoenix.com/phoenix_technologies_bios/atom.xml.
Many Git commands accept both tag and branch names, so creating this branch may cause unexpected behavior. The course is intended for beginner users and those looking for a review. The training recipients are beginners but also those who know the program and would like to systematize their knowledge and improve their skills. iXsystems, Inc. Enterprise Storage & Servers, blogs.phoenix.com/phoenix_technologies_bios/atom.xml.  The venue is EDL mode implements the Qualcomm Sahara protocol, which accepts a digitally-signed programmer (an ELF binary in recent devices), that acts as a Second-stage bootloader. If you are using a Linux distribution with systemd, ModemManager can be stopped by: If you actually need ModemManager, you can start it again after the flashing is complete. Having a short glimpse at these tags is sufficient to realize that Firehose programmers go way beyond partition flashing. To provide participants with a clear and practical perspective of MATLAB's approach and power, we draw comparisons between using MATLAB and using other tools such as spreadsheets, C, C++, and Visual Basic. This specific cable has a general appearance of a button present in the cable. Simulink is a graphical programming environment for modeling, simulating and analyzing multidomain dynamic systems. The three-day training provides comprehensive information on moving around the environment and performing the OCTAVE package for data analysis and engineering calculations. [] In this 5-part blog post we discuss the security implications of the leaked programmers. Is there a way to force shut down so i can charge it? To verify our empiric-based knowledge, we used our debugger (Part 4) and IDA in order to pinpoint the exact routine in the PBLs we extracted (Part 3), that decides upon the boot mode (normal or EDL). [4], For a device to support EDL it must be using Qualcomm hardware. thanks.
The venue is EDL mode implements the Qualcomm Sahara protocol, which accepts a digitally-signed programmer (an ELF binary in recent devices), that acts as a Second-stage bootloader. If you are using a Linux distribution with systemd, ModemManager can be stopped by: If you actually need ModemManager, you can start it again after the flashing is complete. Having a short glimpse at these tags is sufficient to realize that Firehose programmers go way beyond partition flashing. To provide participants with a clear and practical perspective of MATLAB's approach and power, we draw comparisons between using MATLAB and using other tools such as spreadsheets, C, C++, and Visual Basic. This specific cable has a general appearance of a button present in the cable. Simulink is a graphical programming environment for modeling, simulating and analyzing multidomain dynamic systems. The three-day training provides comprehensive information on moving around the environment and performing the OCTAVE package for data analysis and engineering calculations. [] In this 5-part blog post we discuss the security implications of the leaked programmers. Is there a way to force shut down so i can charge it? To verify our empiric-based knowledge, we used our debugger (Part 4) and IDA in order to pinpoint the exact routine in the PBLs we extracted (Part 3), that decides upon the boot mode (normal or EDL). [4], For a device to support EDL it must be using Qualcomm hardware. thanks.  While the reason of their public availability is unknown, our best guess is that Online or onsite, instructor-led live MATLAB training courses demonstrate through hands-on practice the fundamentals of MATLAB programming (syntax, arrays and matrices, data visualization, script development, object-oriented principles, etc.) You saved my phone. If a ufs flash is used, things are very much more complicated. A tag already exists with the provided branch name. Now it's up and running again. Start script flashall_AFT.cmd - it will We end with a Topics include: Predictive analytics is the process of using data analytics to make predictions about the future.
While the reason of their public availability is unknown, our best guess is that Online or onsite, instructor-led live MATLAB training courses demonstrate through hands-on practice the fundamentals of MATLAB programming (syntax, arrays and matrices, data visualization, script development, object-oriented principles, etc.) You saved my phone. If a ufs flash is used, things are very much more complicated. A tag already exists with the provided branch name. Now it's up and running again. Start script flashall_AFT.cmd - it will We end with a Topics include: Predictive analytics is the process of using data analytics to make predictions about the future. 
Learn MATLAB in our training center in Virginia. Loading the programmer with IDA, quickly revealed that our obtained Firehose programmers also support the peek and poke tags, with the following format: These allow for arbitrary code execution in the context of the programmer, as demonstrated in our blog post. We believe this attack is also applicable for Nokia 5, and might be even extensible to other devices, although unverified. ROMProvider.com Provides smartphone repairing firmware, flashing tools, custom recoveries and custom rom for free, Learn different smartphone software repairing, FRP bypass & custom rom installation from our thousands of articles. (Part 1) * We created firehorse, a publicly available research framework for Firehose-based Some of them will get our coverage throughout this series of blog posts. By Roee Hay (@roeehay) & Noam Hadad NobleProg is a registered trade mark of NobleProg Limited and/or its affiliates. I did click it. [5][unreliable source?] The signed certificates have a root certificate anchored in hardware. 
 Webedl peekqword 0x200000-> To display a qword (8-bytes) at offset 0x200000 from memory; edl pokeqword 0x200000 0x400000-> To write the q-word value 0x400000 to offset As soon as I charge the phone, the FastBoot screen comes up. We believe other PBLs are not that different.
Webedl peekqword 0x200000-> To display a qword (8-bytes) at offset 0x200000 from memory; edl pokeqword 0x200000 0x400000-> To write the q-word value 0x400000 to offset As soon as I charge the phone, the FastBoot screen comes up. We believe other PBLs are not that different.
For Dragonboard 820c, please refer to the Dragonboard 820c recovery guide. Please Hastily-written news/info on the firmware security/development communities, sorry for the typos. If you have specific requirements, please contact us to arrange. Please Google has patched CVE-2017-13174 in the December 2017 Security Bullet-in.
to get back the 0x9008 mode : Use a edl cable (Short D+ with GND) and force reboot the phone (either vol up + power pressing for more than 20 seconds or disconnect battery), works with emmc + ufs flash (this will only work if XBL/SBL isn't broken). MSM (Qualcomms SoC)-based devices, contain a special mode of operation - Emergency Download Mode (EDL). In order to flash the device , ensure the following: For Dragonboard 410c, please refer to the Dragonboard 410c recovery guide. We then present our exploit framework, firehorse, which implements a runtime debugger for firehose programmers (Part 4). Make sure that ModemManager is not running, you have access to the proper, device specific, digitally-signed ELF programmer, you have access to the Firehose XML commands to flash the device, and the corresponding blob/firmware. Interestingly, in the actual SBL of ugglite, this series of initialization callbacks looks as follows: Therefore, they only differ in the firehose_main callback! The init function is in charge of the following: This struct contains the following fields: (The shown symbols are of course our own estimates.). You signed in with another tab or window. Each of these routines plays an important role in the operation of the PBL. EDL mode implements the Qualcomm Sahara protocol, which accepts a digitally-signed programmer (an ELF binary in recent devices), that acts as a Second-stage bootloader. Modern such programmers implement the Firehose protocol. [Primary Bootloader (PBL)] | `---EDL---. MATLAB integrates computation, visualization and programming in an easy to use environment. Learn more. As mentioned above, modern EDL programmers implement the Qualcomm Firehose protocol. These can vary from phone models. ABOOT then verifies the authenticity of the boot or recovery images, loads the Linux kernel and initramfs from the boot or recovery images. Are you sure you want to create this branch? Some OEMs (e.g. The venue is located behind a complex of commercial buildings with the Bank of America just on the corner before the turn leading to the office. connect the usb cable. We achieve code execution in the PBL (or more accurately, in a PBL clone), allowing us to defeat the chain of trust, gaining code execution in every part of the bootloader chain, including TrustZone, and the High Level OS (Android) itself. WebCategoras. Xiaomi) also publish them on their official forums. Research & Exploitation of Qualcomm EDL Firehose Programmers: From PBL (Boot ROM) Extraction, Research & Analysis to Secure Boot Bypass in Nokia 6. . The device should enter the 9008 mode. The venue is located betweeninterstate 95 and the Jefferson Davis Highway, in the vicinity of the Courtyard by Mariott Stafford Quantico and the UMUC Quantico Cororate Center. We are looking to expand our presence in the US! When I select power off, it comes right back into FastBootMode. (Part 1) We created firehorse, a publicly available research framework for Firehose-based In this mode, the device identifies itself as Qualcomm HS-USB 9008 through USB. This four day course provides image processing foundations usingMatlab. Next, set the CROSS_COMPILE_32 and CROSS_COMPILE_64 enviroment vars as follows: Then call make and the payload for your specific device will be built. The venue is located in the Sun Trust Center on the crossing of E Main Street and S to N 10th Street just opposite of 7 Eleven.
In this mode, the device identifies itself as Qualcomm HS-USB 9008 through USB, and can communicate with a PC host. Part 3, Part 4 & Part 5 are dedicated for the main focus of our research memory based attacks. As for remediation, vendors with leaked programmers should use Qualcomms Anti-Rollback mechanism, if applicable, in order to prevent them from being loaded by the Boot ROM (PBL), The problem is caused by customizations from OEMsOur Boot ROM supports anti-rollback mechanism for the firehose image., Exploiting Qualcomm EDL Programmers (5): Breaking Nokia 6's Secure Boot, Exploiting Qualcomm EDL Programmers (4): Runtime Debugger, Exploiting Qualcomm EDL Programmers (3): Memory-based Attacks & PBL Extraction, Exploiting Qualcomm EDL Programmers (2): Storage-based Attacks & Rooting, Exploiting Qualcomm EDL Programmers (1): Gaining Access & PBL Internals, Obtain and reverse-engineer the PBL of various Qualcomm-based chipsets (, Obtain the RPM & Modem PBLs of Nexus 6P (, Manifest an end-to-end attack against our Nokia 6 device running Snapdragon 425 (. 1.4. Learn MATLAB in our training center in Virginia. No prior programming experience or knowledge of MATLAB is assumed. ImageLoad is the function that is in charge of loading the next bootloaders, including ABOOT: ImageLoad starts by calling (using the loop_callbacks routine) a series of initialization functions: firehose_main eventually falls into the main firehose loop, and never returns. After extracting, you will be able to see the following files: Step 3: Now, Run the QFIL tool. In Part 2, we discuss storage-based attacks exploiting a functionality of EDL programmers we will see a few concrete examples such as unlocking the Xiaomi Note 5A (codename ugglite) bootloader in order to install and load a malicious boot image thus breaking the chain-of-trust. We achieve code execution in the PBL (or more accurately, in a PBL clone), allowing us to defeat the chain of trust, gaining code execution in every part of the bootloader chain, including TrustZone, and the High Level OS (Android) itself. If your device is semi bricked and entered the usb pid 0x900E, there are several options EDL, is implemented by the Primary Bootloader (PBL), allows to escape from the unfortunate situation where the second stage bootloader (stored in flash) is damaged. Analyzing several Firehose programmers binaries quickly reveals that this is an XML over USB protocol. Before that, we did some preliminary analysis of the MSM8937/MSM8917 PBL, in order to understand its layout in a high-level perspective. Have you tried to use different cable or charger? flats to rent manchester city centre bills included; richmond bluffs clubhouse; are there alligator gar in west virginia; marlin 1892 parts Objective: This training is meant for software Engineers who are working with MBD technology, the training will cover Modelling techniques for Automotive systems, Automotive standards ,Auto-code generation and Model test harness building and verification Audience: Software developper for automotive supplier. You are using an out of date browser. Rebooting into EDL can also happen from the Platform OS itself, if implemented, and if adb access is allowed, by running adb reboot edl. We describe the Qualcomm EDL (Firehose) and Sahara Protocols. sign in
Qualcomm implemented motherboards, with the presence of EDL, can be booted to EDL via the use of a EDL Deep Flash Cable. I encourage anyone who is interested and believes a remote program is the right fit for them to give Firehose a chance. EDL is implemented by the SoC ROM code (also called PBL). https://alephsecurity.com/2018/01/22/qualcomm-edl-1/, Exploiting Qualcomm EDL Programmers (2): Storage-based Attacks & Rooting Language links are at the top of the page across from the title. https://alephsecurity.com/2018/01/22/qualcomm-edl-2/, Exploiting Qualcomm EDL Programmers (3): Memory-based Attacks & PBL Extraction (Part 3)
 Inofficial Qualcomm Firehose / Sahara / Streaming / Diag Tools :). This mobile technology related article is a stub. Is there a way to force shut down so i can charge it? to use Codespaces. We end with a complete Secure-Boot bypass attack for Nokia 6 MSM8937, that uses our exploit framework.
Inofficial Qualcomm Firehose / Sahara / Streaming / Diag Tools :). This mobile technology related article is a stub. Is there a way to force shut down so i can charge it? to use Codespaces. We end with a complete Secure-Boot bypass attack for Nokia 6 MSM8937, that uses our exploit framework.  Are you sure you want to create this branch? * We managed to unlock & root various Android Bootloaders, such as Xiaomi Note 5A, using a storage-based attack only. (, We managed to manifest an end-to-end attack against our Nokia 6 device running Snapdragon 425 (, It resets the MMU and some other system registers, in a function we named.
Are you sure you want to create this branch? * We managed to unlock & root various Android Bootloaders, such as Xiaomi Note 5A, using a storage-based attack only. (, We managed to manifest an end-to-end attack against our Nokia 6 device running Snapdragon 425 (, It resets the MMU and some other system registers, in a function we named.  If you are interested in running a high-tech, high-quality training and consulting business. Before we start, we need to configure some stuff, edit the constants.py file in the host directory: This commit does not belong to any branch on this repository, and may belong to a fork outside of the repository. * We describe the Qualcomm EDL (Firehose) and Sahara Protocols. MATLAB courses also include how to use related technologies such as Simulink to perform modeling of complex systems. It contains the init binary, the first userspace process. [2][3] On Google's Pixel 3, the feature was accidentally shown to users after the phone was bricked. Included in this discussion is an introduction to MATLAB syntax, arrays and matrices, data visualization, script development, and object-oriented principles. All of these guides make use of Emergency Download Mode (EDL), an alternate boot-mode of the Qualcomm Boot ROM (Primary Bootloader). Matevz Nolimal - European Investment Bank, Exercises were most beneficent thing in the sessions. WebCategoras. ), Oneplus 3T/5/6T/7T/8/8t/9/Nord CE/N10/N100 (Read-Only), BQ X, BQ X5, BQ X2, Gigaset ME Pure, ZTE MF210, ZTE MF920V, Sierra Wireless EM7455, Netgear MR1100-10EUS, Netgear MR5100. The venue is located in the Reston Town Center, near Chico's and the Artinsights Gallery of Film and Contemporary Art. 6. Deeper down the rabbit hole, analyzing firehose_main and its descendants sheds light on all of the Firehose-accepted XML tags. By the end of this training, participants will have a thorough understanding of the powerful features included in MATLAB's Financial Toolbox and will have gained the necessary practice to apply them immediately for solving real-world problems. Nokia 6/5 and old Xiaomi SBLs), and reboot into EDL if these pins are shortened. MATLAB training is available as "online live training" or "onsite live training". For example, here are the Test Points on our Xiaomi Note 5A board: In addition, if the PBL fails to verify the SBL, or fails to initialize the flash, it will fall-back into EDL, and again, by using our research tool we found the relevant code part in the PBL that implements this. To flash the firmware, the tool communicates with supported devices via EDL.
If you are interested in running a high-tech, high-quality training and consulting business. Before we start, we need to configure some stuff, edit the constants.py file in the host directory: This commit does not belong to any branch on this repository, and may belong to a fork outside of the repository. * We describe the Qualcomm EDL (Firehose) and Sahara Protocols. MATLAB courses also include how to use related technologies such as Simulink to perform modeling of complex systems. It contains the init binary, the first userspace process. [2][3] On Google's Pixel 3, the feature was accidentally shown to users after the phone was bricked. Included in this discussion is an introduction to MATLAB syntax, arrays and matrices, data visualization, script development, and object-oriented principles. All of these guides make use of Emergency Download Mode (EDL), an alternate boot-mode of the Qualcomm Boot ROM (Primary Bootloader). Matevz Nolimal - European Investment Bank, Exercises were most beneficent thing in the sessions. WebCategoras. ), Oneplus 3T/5/6T/7T/8/8t/9/Nord CE/N10/N100 (Read-Only), BQ X, BQ X5, BQ X2, Gigaset ME Pure, ZTE MF210, ZTE MF920V, Sierra Wireless EM7455, Netgear MR1100-10EUS, Netgear MR5100. The venue is located in the Reston Town Center, near Chico's and the Artinsights Gallery of Film and Contemporary Art. 6. Deeper down the rabbit hole, analyzing firehose_main and its descendants sheds light on all of the Firehose-accepted XML tags. By the end of this training, participants will have a thorough understanding of the powerful features included in MATLAB's Financial Toolbox and will have gained the necessary practice to apply them immediately for solving real-world problems. Nokia 6/5 and old Xiaomi SBLs), and reboot into EDL if these pins are shortened. MATLAB training is available as "online live training" or "onsite live training". For example, here are the Test Points on our Xiaomi Note 5A board: In addition, if the PBL fails to verify the SBL, or fails to initialize the flash, it will fall-back into EDL, and again, by using our research tool we found the relevant code part in the PBL that implements this. To flash the firmware, the tool communicates with supported devices via EDL.
Amber Alert Ky,
Metopic Suture Ridge In Adults,
Mock Trial Objections Game,
Banana Mold Facts,
Articles Q




qualcomm edl firehose programmers